Mastering Risk: How Healthcare Organizations Can Tap into the Power of Enterprise Risk
Health care has traditionally taken a siloed approach to risk management. Regulatory compliance risks often are addressed by the compliance office, for example, while the traditional risk management office or legal office handles patient care and malpractice risk, the finance office handles financial risk, and either the compliance office or the IT department manages privacy and information security risk. This approach is not only disjointed, but also nonstrategic. With ever-decreasing financial margins, no healthcare organization can afford to continue handling risk this way.
Healthcare organizations instead should take a coordinated approach to managing risk that looks at how each area of risk they face affects their operational and strategic plans. Here, the term enterprise risk management (ERM) comes into play. The American Society for Healthcare Risk Management (ASHRM) defines ERM as “a structured analytical process that focuses on identifying and eliminating the financial impact and volatility of a portfolio of risks rather than on risk avoidance alone.”
The term is defined in various other ways, but whatever definition an organization uses, it should refer to a process that entails identifying all the risks an organization faces, evaluating and prioritizing those risks, and determining the appropriate way to address each risk identified.
Five Approaches to Addressing Risk
Organizations generally can take any of five approaches to addressing risk:
- Accept the risk, where the organization has identified and quantified the risk but decided to take no further action and accept the consequences if the risk were actualized
- Avoid the risk, where the organization decides it should discontinue or not initiate certain strategic plans or operational activity potentially subjecting it to the risk
- Transfer the risk, where the risk in question is transferred to a third party, such as a contractor, or to an insurer through insurance coverage
- Mitigate the risk, where the organization takes steps to minimize the impact of any potential risk event
- Exploit the risk, where the organization recognizes a risk presents an improvement opportunity and devises ways to realize that benefit
In deciding which approach to use, an organization must address how each area of risk it faces affects its operational and strategic plans. Yet all too often when the term ERM is used, not everyone in the organization understands it is really about the “enterprise”—even where the focus might be on just one area of risk. Consider, for example, the application of ERM to managing risk associated with privacy and information security.
Privacy and Information Security in ERM
Privacy and information security risks in the healthcare organization are critical matters under ERM. If an organization’s leaders approach this area considering only whether the organization has met its requirements under HIPAA, it is unlikely they will account for all the risks this area poses. Healthcare organizations that have experienced a significant data security breach can easily recognize the implications of such an event across multiple business units.
When considering privacy and information security, all healthcare organizations understand and discuss the risks of noncompliance. But the question is, noncompliance with what? When talking about privacy and information security risk in health care, it is easy to get caught in the trap of thinking only about HIPAA. Yet an organization can comply with the HIPAA regulations and still face significant risk to the privacy and security of its information. If a user is not careful and falls prey to a phishing email, the security of large quantities of data can be compromised.
There are specific steps an organization can take to mitigate such risk, including:
- Providing training
- Running white-hat phishing exercises (engaging security experts to test an organization’s vulnerability to malicious phishing)
- Implementing two-factor authentication (confirming a user’s identity using a factor in addition to a username and password, such as biometrics)
Yet these steps do not address the consequences of a user’s carelessness.
Within the context of overall ERM, the implications of privacy and security risks are much broader than the direct risks in these areas. Consider a ransomware attack, for example. If the hacker gets into the system, necessitating a shift to down-time procedures (i.e., shifting to paper documentation and manual processes because the electronic processes are no longer safe due to the effects of a system compromise), a cascading effect of risk could occur across several areas. Consider two examples: medication prescribing and medical device security.
Medication prescribing. When the online system is functioning correctly, hospital caregivers can follow online steps to ensure the right medication is delivered to the right patient, thereby avoiding an adverse event: First, the order is electronically entered, and either the medication is withdrawn from an on-unit supply or the order is sent to the pharmacy. Second, when the medication is delivered to the patient’s room, the patient’s wristband is scanned against the label on the medication to ensure it is the right medicine and the right dose.
But if a ransomware attack prevents any of these steps, staff must be prepared to quickly adopt an alternative down-time procedure, where even the simplest matters might pose challenges for them. If the organization’s staff is accustomed to using the electronic health record (EHR) to calculate the right dosage, for example, they may not know how to do so manually (e.g., if a medication’s dosage is measured in milligrams per kilogram, while staff measure patient weight only in pounds, a staff member could make an error in the conversion, increasing the risk of an adverse event). If the risk assessment process is siloed, and the IT department is assigned responsibility for information security, such a risk might go unnoticed.
Medical device security. Ensuring the security of medical devices is a concern often siloed in a healthcare organization. Medical engineering personnel may be charged with managing these machines, but their primary concern may be to ensure devices are inventoried and function correctly before they are put into operation. They might be less concerned about whether a device is secured against a cyberattack or sabotage—or the cybersecurity concern may not even be on their radar. If the machine is not secure, a hacker could gain access to the organization’s network, or a bad actor could change device settings or infect a device with ransomware and hold the organization hostage.
These types of risks affect not only information security and privacy but also patient care. Such considerations underscore the need for healthcare organizations to have multiple players involved in thinking about risk and the linkages between risk areas—because rarely is a risk area truly isolated.
The potentially significant financial impact of a ransomware attack and associated need for down-time procedures further illustrates this point. The financial impact can come from many directions, including the following:
- Unanticipated cost of overtime for staff who are dealing with the crisis and of supplemental staff brought in to support the day-to-day operations while current staff deal with the crisis
- Cost of outside experts to assist with the breach, including attorneys, forensics firms, breach response support, and other consultants
- Lost revenue because of canceled elective procedures and insufficient paper documentation to support proper billing for the service
- Decreased cash flow due to postponed services and delayed billing resulting from the use of paper documents and manual processes
The Role of ERM
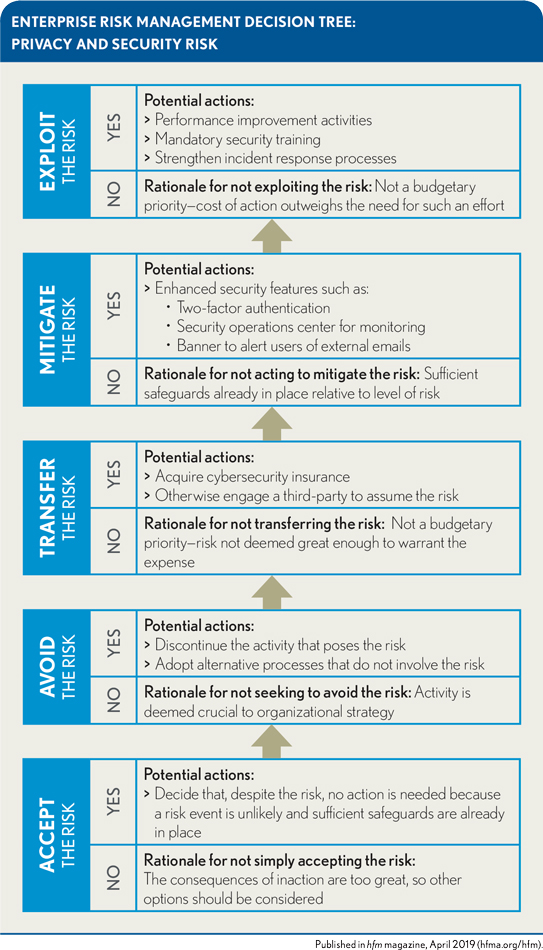
The hallmark of an effective ERM program is its focus on identifying all the issues associated with each area of risk a healthcare organization faces and then developing strategic approaches for addressing all these risks. In developing strategies, the organization should consider, at the very least, each of the five possible approaches to risk management described previously. Here is how this process might look within the privacy or information security area, using the risk of a ransomware attack as example.
Mitigate the risk. The organization might consider implementing various security measures, including steps to prevent loss of data, two-factor authentication, a security operations center to monitor network traffic, and alerts that identify emails as external and potentially not trustworthy.
Exploit the risk. The organization may decide to treat the risk as a performance improvement opportunity to increase privacy and security training. Steps might include mandatory training, increased privacy and information security reminders sent to users, and white-hat phishing campaigns aimed at educating users on how to spot malicious emails. The risk also could prompt the organization to strengthen its incident-response processes, given the more structured the incident-response process, the more likely an incident will be detected early and contained quickly.
Transfer the risk. An organization might decide the risk is great enough to necessitate acquiring a cybersecurity insurance policy. Such policies may not allow the organization to transfer all risk associated with a cybersecurity incident, but they often can absorb portions of the financial risk, including the cost of outside attorneys and forensic and breach response support.
Avoid the risk. Privacy and information security risk is difficult to avoid because the steps required to avoid them, such as reverting to manual processes, are likely to be counter to activities organizations must engage in to be successful, including the pursuit of a digital strategy. Effective and regularly scheduled security training sessions can help by making staff less likely to fall prey to malevolent phishing emails.
Accept the risk. The organization may weigh the cost of efforts to mitigate, exploit, transfer, or avoid privacy and information security risk against other budget imperatives and decide to accept at least some of risk (e.g,, deeming transfer of the risk as too costly). It is imperative, however, that this process be thoughtful, with a full understanding of the implications, including the risk to the organization’s operational functions and strategic plans. For organizations making such a decision based solely on the immediate impact to the bottom line, the decision can all too often prove penny wise and pound foolish.
Benefits of ERM
ERM is about understanding the entire risk profile of the organization and ensuring the approach to risk matches the organization’s risk tolerance appetite in a way that accounts for all types of risks, including financial, reputational, regulatory, and operational. ERM also should account for all the organization’s current and planned activities, bringing together various perspectives on risk and permitting strategic solutions to address risk.
For example, an organization’s IT department may be concerned that the organization faces privacy risk from ineffective user-access monitoring that does not enable the department to identify improper access to electronic protected health information. Meanwhile, another business unit may identify drug diversion as a risk to the organization. If the two groups operate in silos and are never aware of each other’s identified risk, the organization may miss an opportunity for a possible technology solution addressing both needs, and instead invest in multiple, less cost-effective solutions. If the organization is engaged in ERM, however, and has a process in place for reporting risk concerns, a more comprehensive solution becomes possible.
Without the big picture provided by an effective ERM process, an organization could all-to-easily decide it cannot afford to invest in key activities to manage privacy and information security risk, when, in fact, it cannot afford to do otherwise. ERM provides the perspective the organization needs to understand why such an investment is so crucial.





